13 Information Security Risk Assessment Procedure Example Docx

13 Information Security Risk Assessment Procedure Example Docx Easily identify and assess cybersecurity risk with this simple cybersecurity risk assessment template. this template enables you to customize a risk rating key to suit your cybersecurity criteria. the template includes pre built risk level scoring, so you and your team can determine the acceptable level of risk for each aspect of your business. Extent determined necessary by the secretary to improve the efficiency of operation or security of federal information systems. standards prescribed shall include information security standards that provide minimum information security requirements and are otherwise necessary to improve the security of federal information and information.
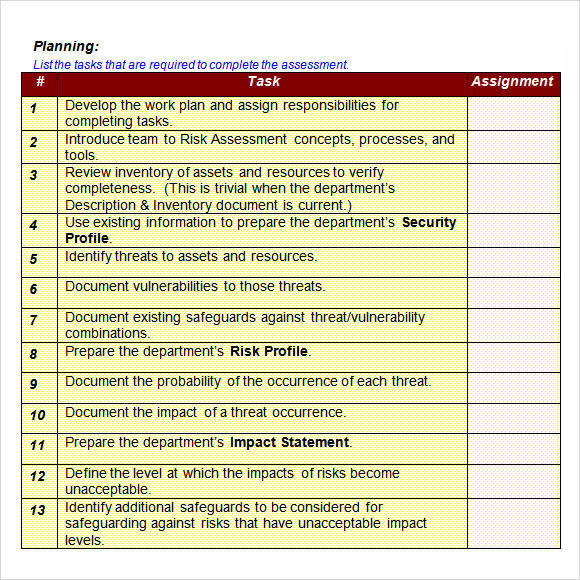
Free 11 Sample It Risk Assessment Templates In Pdf Ms Word Excel We’ve compiled the most useful free iso 27001 information security standard checklists and templates, including templates for it, hr, data centers, and surveillance, as well as details for how to fill in these templates. included on this page, you'll find an iso 27001 checklist and an iso 27001 risk assessment template, as well as an up to. The four phases of nist risk assessment. nist outlines four primary steps in the ra process: 1) prepare for the assessment; 2) conduct the assessment; 3) communicate the assessment results; and 4) maintain the assessment. some steps are further divided into subtasks, as outlined below. 1. Apply the information security risk assessment process to identify risks. identify risk owners. analyses the information security risks. assess the potential consequences that would result if the risks were to materialise. assess the realistic likelihood of the occurrence of the risks identified. determine the levels of risk. The current 2022 revision of iso 27001 allows you to identify risks using any methodology you like; however, the methodology called “asset based risk assessment” (defined by the old 2005 revision of iso 27001) is still dominating, and it requires identification of assets, threats, and vulnerabilities.
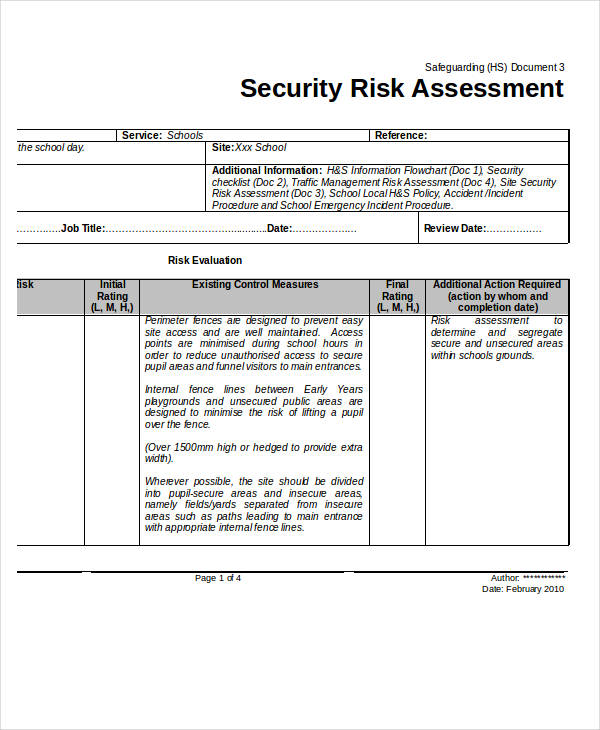
Risk Assessment 45 Examples Pdf Doc Apply the information security risk assessment process to identify risks. identify risk owners. analyses the information security risks. assess the potential consequences that would result if the risks were to materialise. assess the realistic likelihood of the occurrence of the risks identified. determine the levels of risk. The current 2022 revision of iso 27001 allows you to identify risks using any methodology you like; however, the methodology called “asset based risk assessment” (defined by the old 2005 revision of iso 27001) is still dominating, and it requires identification of assets, threats, and vulnerabilities. Procedures related to risk assessment for information systems. 2.2 chief information officer (cio) directives the cms chief information officer (cio), the cms chief information security officer (ciso),. An information security risk assessment is a formal, top management driven process and sits at the core of an iso 27001 information security management system (isms). there are five simple steps that you should take to conduct a successful risk assessment: establish a risk management framework. identify risks. analyse risks.

10 Security Risk Assessment Templates Free Samples Examples Procedures related to risk assessment for information systems. 2.2 chief information officer (cio) directives the cms chief information officer (cio), the cms chief information security officer (ciso),. An information security risk assessment is a formal, top management driven process and sits at the core of an iso 27001 information security management system (isms). there are five simple steps that you should take to conduct a successful risk assessment: establish a risk management framework. identify risks. analyse risks.

Comments are closed.