5 Steps To Cloud Security Assessment Zindagi Technologies

5 Steps To Cloud Security Assessment Zindagi Technologies The organization should conduct the security assessment of the present and future cloud deployments as this is a critical part of the process. 5 steps of cloud security assessment. cloud security is not easy and its assessment is difficult too as it takes time and resources and good experience to accomplish and in the following 5 steps, we will. Here are the 5 key steps to take for a complete cloud risk assessment checklist, to act as a supplement to your main cloud assessment tools: step one: identify your assets. the first step in performing a cloud security assessment is identifying all of the assets that are stored in your cloud environment.
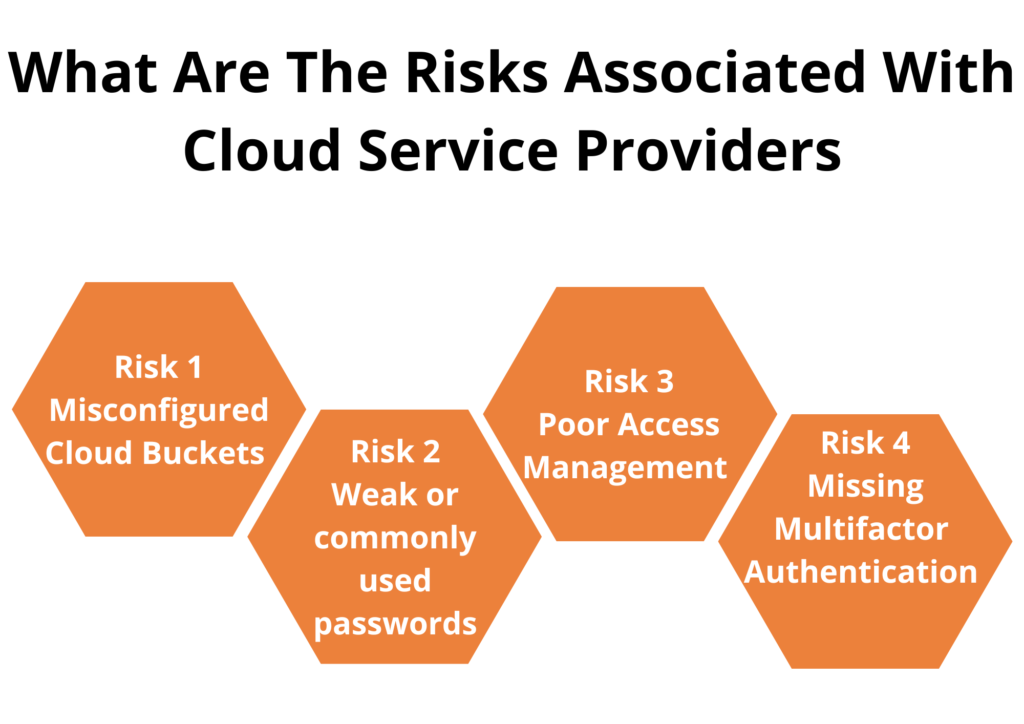
5 Steps To Cloud Security Assessment Zindagi Technologies To prepare for a cloud security assessment, begin by evaluating your existing infrastructure and security measures. this could help you easily define your objectives. allocate resources and set a. One way that security and cloud engineering teams can minimize trouble is by conducting a cloud security assessment, a process that can enable organizations to discover their weak points before adversaries do. a cloud security assessment evaluates the cloud infrastructure for vulnerabilities, configuration weaknesses and potential threats. The assessment can cover various aspects of cloud security, including data privacy, data integrity, access control, identity and access management (iam), network security, and compliance with relevant laws and regulations. it can be performed by internal security teams or by third party security experts who are specialized in cloud security. 6 steps to execute a cloud security assessment. the six steps to execute a cloud security assessment are: 1. define the scope of the assessment. the initial step involves defining the scope of the cloud security assessment to ensure comprehensive evaluation.

5 Steps To Cloud Security Assessment Zindagi Technologies The assessment can cover various aspects of cloud security, including data privacy, data integrity, access control, identity and access management (iam), network security, and compliance with relevant laws and regulations. it can be performed by internal security teams or by third party security experts who are specialized in cloud security. 6 steps to execute a cloud security assessment. the six steps to execute a cloud security assessment are: 1. define the scope of the assessment. the initial step involves defining the scope of the cloud security assessment to ensure comprehensive evaluation. The basics of cloud security assessment. cloud security assessment boils down to three key stages: auditing everything that runs in the cloud environment. pinpointing the possible attack vectors based on the detected vulnerabilities. prioritizing the remediation actions to shield the most valuable organizational assets. Then, over time, ensure that security teams are regularly auditing permission rights and monitoring user activity in the cloud. 4. establish external sharing standards. one of the major benefits of the cloud is convenience. it has made accessing and sharing information across the enterprise a breeze.

How To Conduct A Cloud Security Assessment 5 Steps The basics of cloud security assessment. cloud security assessment boils down to three key stages: auditing everything that runs in the cloud environment. pinpointing the possible attack vectors based on the detected vulnerabilities. prioritizing the remediation actions to shield the most valuable organizational assets. Then, over time, ensure that security teams are regularly auditing permission rights and monitoring user activity in the cloud. 4. establish external sharing standards. one of the major benefits of the cloud is convenience. it has made accessing and sharing information across the enterprise a breeze.

Comments are closed.