A Detailed Guide To The Different Types Of Cyber Security Threats Dtc

A Detailed Guide To The Different Types Of Cyber Security Threats Dtc Cyber security threats are becoming more and more common, and it’s important to be aware of the different types that exist. this guide has provided an overview of some of the most common types of cyber security threats, as well as some tips on how to protect yourself from them. remember to stay vigilant and keep your computer security up to. 1. malware. malware — or malicious software — is any program or code that is created with the intent to do harm to a computer, network or server. malware is the most common type of cyberattack, mostly because this term encompasses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, cryptojacking, and any.

A Detailed Guide To The Different Types Of Cyber Security Threats Dtc Understanding the ever evolving landscape of cyber threats is vital for every individual and business entity in our increasingly digital world. cyber threats range from simple to incredibly complex, and understanding the different threat types can empower you to adopt the right strategies to guard against them. this comprehensive guide to cybersecurity provides a detailed overview of cyber. Cybersecurity threats are acts performed by individuals with harmful intent, whose goal is to steal data, cause damage to or disrupt computing systems. common categories of cyber threats include malware, social engineering, man in the middle (mitm) attacks, denial of service (dos), and injection attacks—we describe each of these categories in. Attackers are also harnessing the power of ai tools to improve attack techniques and direct their networks of slave machines to perform ddos attacks accordingly. worryingly, ai is now being used to enhance all forms of cyberattacks, although it has potential cybersecurity uses, too. 5. phishing. Cybersecurity is a set of practices used to protect computer systems, networks, and data from digital attacks, unauthorized access, damage, or theft. it involves a range of strategies, technologies, and best practices designed to keep the information safe. it covers everything from password management to computer security tools.
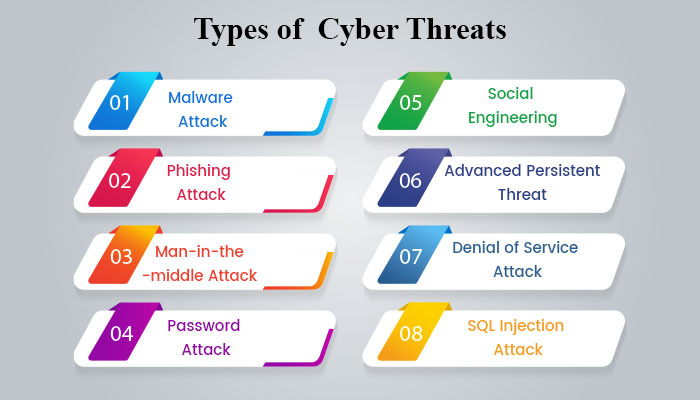
Cyber Security Types And Threats Defined Detailed Guide Attackers are also harnessing the power of ai tools to improve attack techniques and direct their networks of slave machines to perform ddos attacks accordingly. worryingly, ai is now being used to enhance all forms of cyberattacks, although it has potential cybersecurity uses, too. 5. phishing. Cybersecurity is a set of practices used to protect computer systems, networks, and data from digital attacks, unauthorized access, damage, or theft. it involves a range of strategies, technologies, and best practices designed to keep the information safe. it covers everything from password management to computer security tools. Cybersecurity threats reflect the risk of experiencing a cyberattack. a cyberattack is an intentional and malicious effort by an organization or an individual to breach the systems of another organization or individual. the attacker’s motives may include information theft, financial gain, espionage, or sabotage. Top 20 most common types of cybersecurity attacks. 1. dos and ddos attacks. a denial of service (dos) attack is designed to overwhelm the resources of a system to the point where it is unable to reply to legitimate service requests. a distributed denial of service (ddos) attack is similar in that it also seeks to drain the resources of a system.

Comments are closed.