Free 12 Sample Security Risk Assessment Templates In Pdf Ms Word
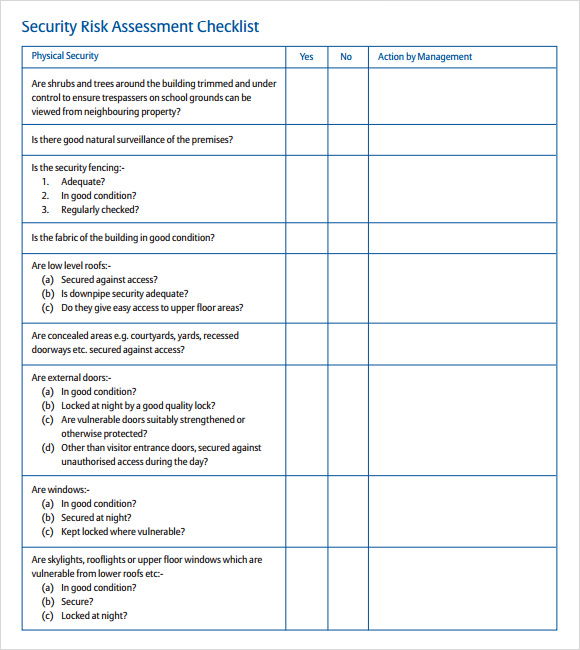
Free 12 Sample Security Risk Assessment Templates In Pdf Ms Word Excel Average rating 5. vote count: # assessment # security. 26 free printable apartment make ready checklist form templates. 20 free lifting equipment audit checklist templates (pdf, doc) a security risk assessment template is a document that outlines the steps and processes for conducting a comprehensive evaluation of various security threats. Target audience of a security risk assessment template. 1. people shifting to a new place. 2. banks and other financial institutions, and people who are giving their money to them. 3. people sharing their personal and financial information online. you may also see it security policy templates. 4.
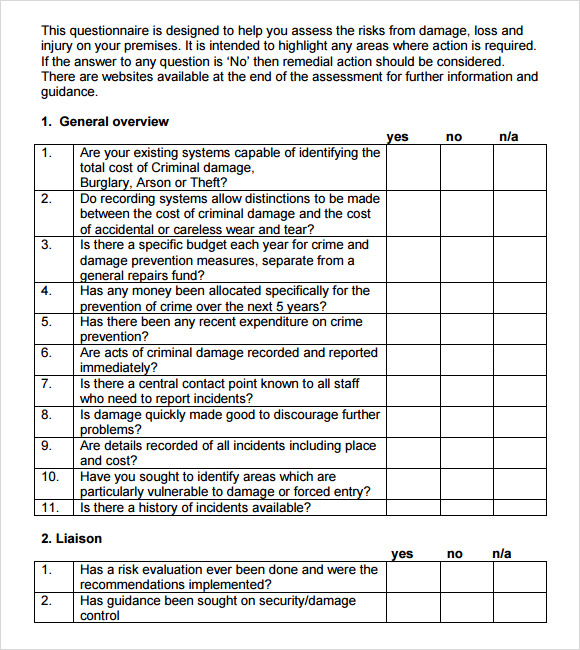
Free 12 Sample Security Risk Assessment Templates In Pdf Ms Word Excel Easily identify and assess cybersecurity risk with this simple cybersecurity risk assessment template. this template enables you to customize a risk rating key to suit your cybersecurity criteria. the template includes pre built risk level scoring, so you and your team can determine the acceptable level of risk for each aspect of your business. Security risk assessment is the process of identifying risks that an organization is exposed to, the probability of such risks, and the consequences that may arise from such risks. a structured risk assessment template helps streamline this process. it helps guide the assessors through key steps such as documenting changes, introducing the. Your toolkit of free cybersecurity risk assessment templates. we understand the diverse needs of our audience, which is why we offer cybersecurity risk assessment templates in three different formats: 1. pdf template. ideal for those seeking a static format for printing or sharing digitally, our pdf template is secure and user friendly. A security risk assessment template is a structured document or tool that serves as the foundation for conducting a thorough and consistent evaluation of an organization’s information security posture. it is designed to facilitate the identification, analysis, and prioritization of security risks that may compromise the confidentiality.
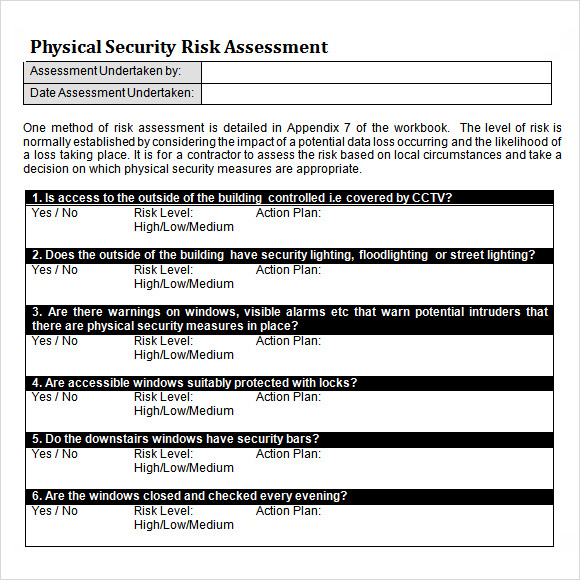
Free 12 Sample Security Risk Assessment Templates In Pdf Ms Word Excel Your toolkit of free cybersecurity risk assessment templates. we understand the diverse needs of our audience, which is why we offer cybersecurity risk assessment templates in three different formats: 1. pdf template. ideal for those seeking a static format for printing or sharing digitally, our pdf template is secure and user friendly. A security risk assessment template is a structured document or tool that serves as the foundation for conducting a thorough and consistent evaluation of an organization’s information security posture. it is designed to facilitate the identification, analysis, and prioritization of security risks that may compromise the confidentiality. Use this risk assessment template to assess and classify hazards related to biological, chemical, environmental, machinery, and other potential risks that impact health and safety. select the impact, probability, and risk level for each hazard, and then establish control measures to reduce risk severity and likelihood. Step 1: identify the hazards. the first step in a risk assessment is identifying potential hazards. these could be physical hazards (e.g., in a construction site), cybersecurity hazards (e.g., potential data breaches), or operational hazards (e.g., a key supplier failing to deliver). to identify hazards:.
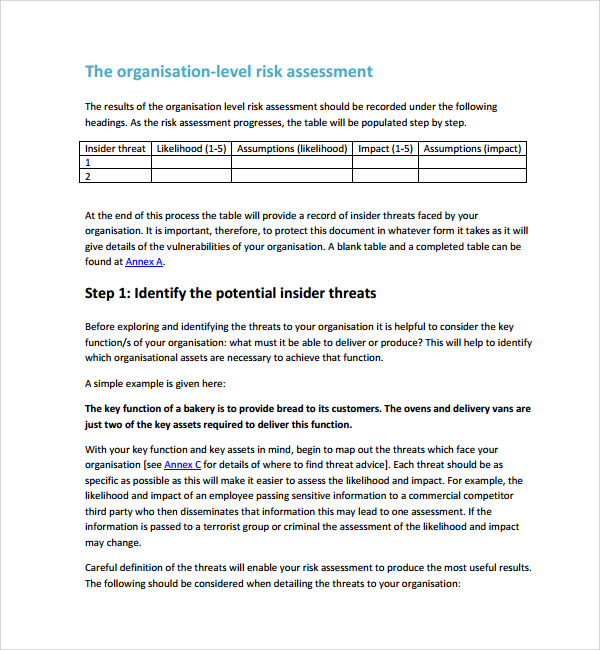
Free 12 Sample Security Risk Assessment Templates In Pdf Ms Word Excel Use this risk assessment template to assess and classify hazards related to biological, chemical, environmental, machinery, and other potential risks that impact health and safety. select the impact, probability, and risk level for each hazard, and then establish control measures to reduce risk severity and likelihood. Step 1: identify the hazards. the first step in a risk assessment is identifying potential hazards. these could be physical hazards (e.g., in a construction site), cybersecurity hazards (e.g., potential data breaches), or operational hazards (e.g., a key supplier failing to deliver). to identify hazards:.

Comments are closed.