How To Conduct A Cloud Security Assessment 5 Steps

How To Conduct A Cloud Security Assessment 5 Steps Here are the 5 key steps to take for a complete cloud risk assessment checklist, to act as a supplement to your main cloud assessment tools: step one: identify your assets. the first step in performing a cloud security assessment is identifying all of the assets that are stored in your cloud environment. How to conduct cloud security assessment in 10 steps. after creating a cloud security assessment checklist, you can now begin the assessment by setting boundaries, identifying requirements, and.
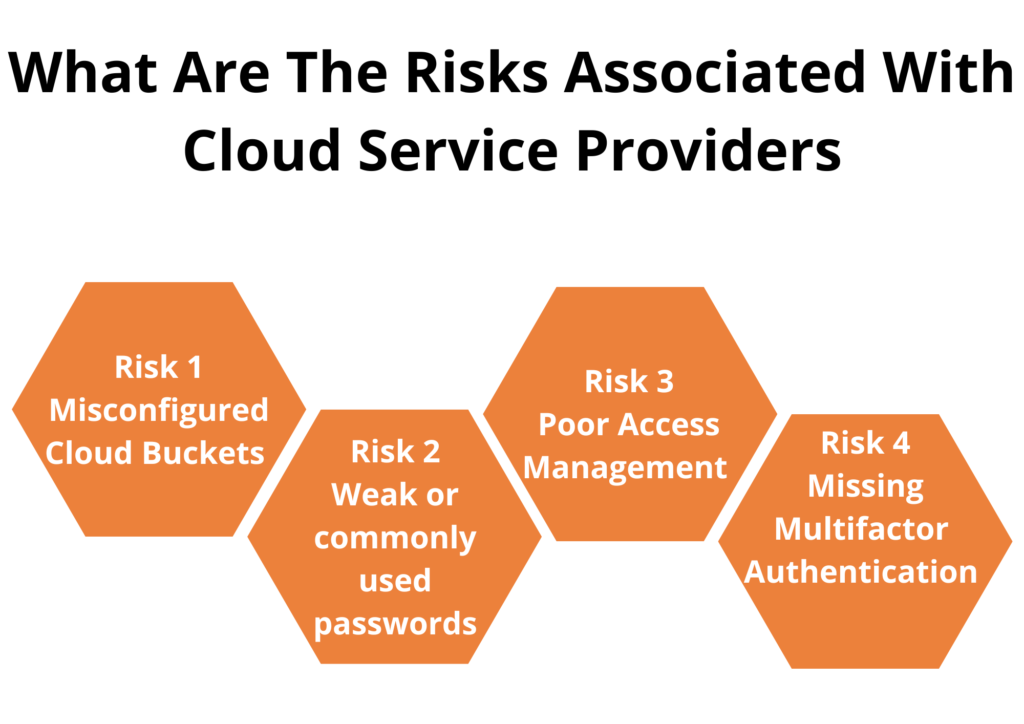
5 Steps To Cloud Security Assessment Zindagi Technologies One way that security and cloud engineering teams can minimize trouble is by conducting a cloud security assessment, a process that can enable organizations to discover their weak points before adversaries do. a cloud security assessment evaluates the cloud infrastructure for vulnerabilities, configuration weaknesses and potential threats. Then, over time, ensure that security teams are regularly auditing permission rights and monitoring user activity in the cloud. 4. establish external sharing standards. one of the major benefits of the cloud is convenience. it has made accessing and sharing information across the enterprise a breeze. The assessment can cover various aspects of cloud security, including data privacy, data integrity, access control, identity and access management (iam), network security, and compliance with relevant laws and regulations. it can be performed by internal security teams or by third party security experts who are specialized in cloud security. Step 1 – identifying cloud assets. the first step of the cloud security assessment checklist is identifying various cloud resources and assets. it includes financial records, customer data, trade secrets, and other company details. all data stored on the cloud, including hidden assets, is identified to prepare for threats and protect against.

5 Steps To Cloud Security Assessment Zindagi Technologies The assessment can cover various aspects of cloud security, including data privacy, data integrity, access control, identity and access management (iam), network security, and compliance with relevant laws and regulations. it can be performed by internal security teams or by third party security experts who are specialized in cloud security. Step 1 – identifying cloud assets. the first step of the cloud security assessment checklist is identifying various cloud resources and assets. it includes financial records, customer data, trade secrets, and other company details. all data stored on the cloud, including hidden assets, is identified to prepare for threats and protect against. The first step in performing a cloud security assessment is to identify all of the assets that are stored in your cloud environment. this includes everything from customer information and. A cloud security assessment is a thorough review of your organization's cloud infrastructure to identify potential vulnerabilities and threats. the process includes analyzing the appropriateness of existing security measures, assessing compliance with industry standards, and testing for potential attacks that could compromise sensitive data.

What Is Cloud Security Assessment Steps To Perform Sprinto The first step in performing a cloud security assessment is to identify all of the assets that are stored in your cloud environment. this includes everything from customer information and. A cloud security assessment is a thorough review of your organization's cloud infrastructure to identify potential vulnerabilities and threats. the process includes analyzing the appropriateness of existing security measures, assessing compliance with industry standards, and testing for potential attacks that could compromise sensitive data.

How To Conduct A Cloud Security Assessment Iemlabs Blog

Comments are closed.