Owasp Top 10 2021 Released Cyber Security News
Owasp Top 10 2021 Released Cyber Security News For the owasp top 10 2021 list, owasp team was also focused on the use of data for exploitability and impact. also they have downloaded owasp dependency check and extracted the cvss exploit, and impact scores grouped by related cwes. “to calculate a top 10 list, the owasp team grouped all the cves with cvss scores by cwe and weighted both. Welcome to the latest installment of the owasp top 10! the owasp top 10 2021 is all new, with a new graphic design and an available one page infographic you can print or obtain from our home page. a huge thank you to everyone that contributed their time and data for this iteration. without you, this installment would not happen.

Owasp Top 10 2021 Released Cyber Security News A09:2021 security logging and monitoring failures was previously insufficient logging & monitoring and is added from the industry survey (#3), moving up from #10 previously. this category is expanded to include more types of failures, is challenging to test for, and isn't well represented in the cve cvss data. The owasp top 10 is a standard awareness document for developers and web application security. it represents a broad consensus about the most critical security risks to web applications. globally recognized by developers as the first step towards more secure coding. companies should adopt this document and start the process of ensuring that. In owasp top 10 2021, broken access control has taken the lead as the category with the most serious web application security risks. the category was fifth in the previous version. there are 34 common weakness enumerations (cwes) mapped to broken access control, and they had the highest number of occurrences (at roughly 318,000) compared to any. New category: insecure design and the need to shift left. as you scan the new top 10, you’ll notice a brand new category in the number four position: insecure design. this focuses on risks.
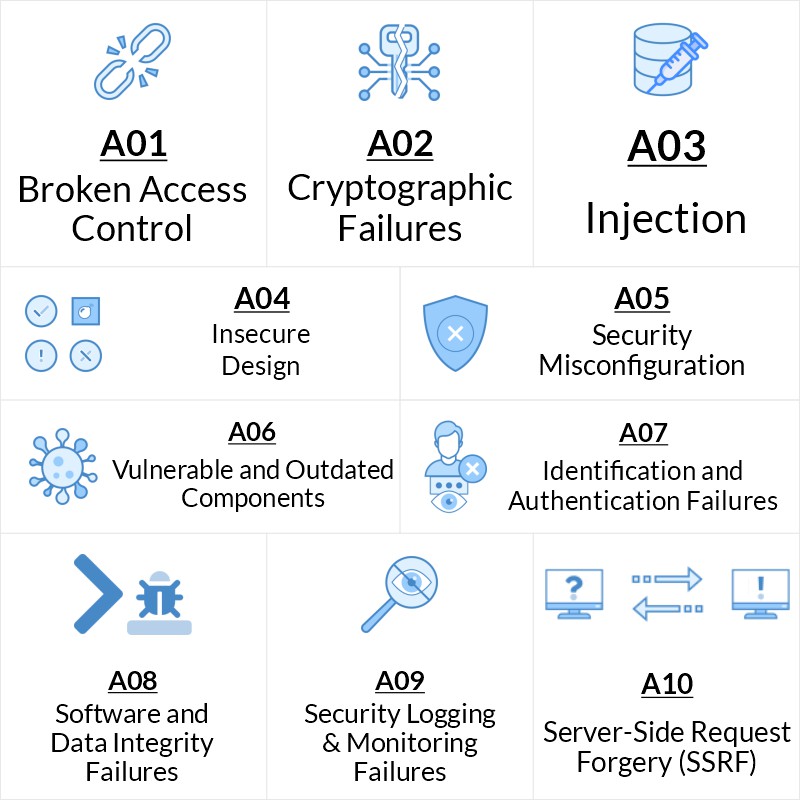
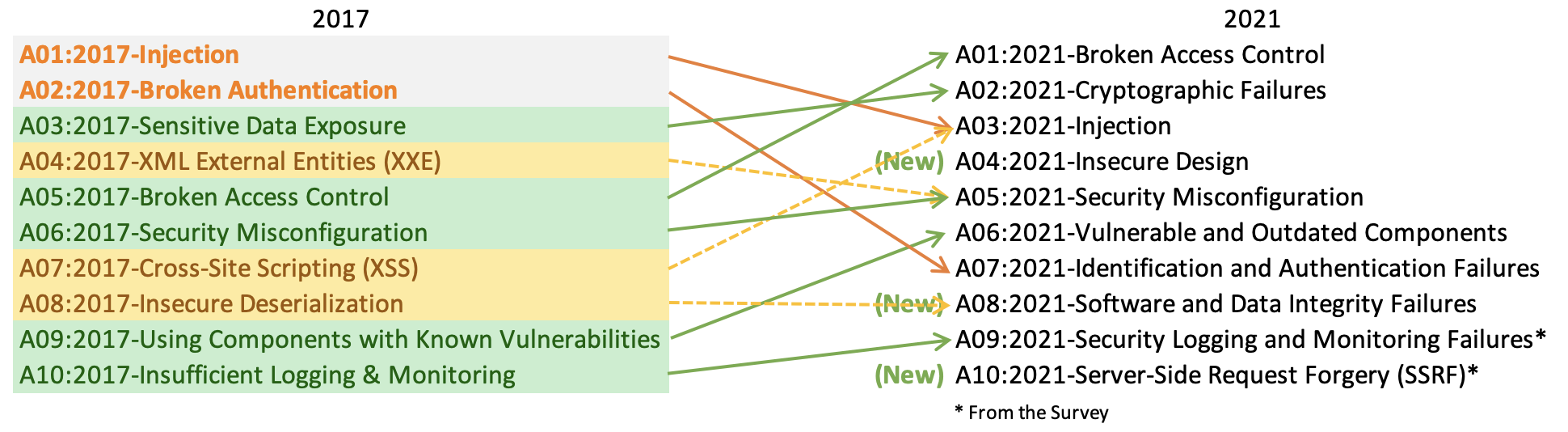
Owasp Top 10 2021 Threat Levels Scenarios Euriun Technologies In owasp top 10 2021, broken access control has taken the lead as the category with the most serious web application security risks. the category was fifth in the previous version. there are 34 common weakness enumerations (cwes) mapped to broken access control, and they had the highest number of occurrences (at roughly 318,000) compared to any. New category: insecure design and the need to shift left. as you scan the new top 10, you’ll notice a brand new category in the number four position: insecure design. this focuses on risks. Non profit confirms latest iteration of web attack hit list during 24 hour live event. owasp celebrated its 20th anniversary last week with a 24 hour webinar that saw the organization officially launch the top 10 web security vulnerabilities for 2021. the online conference, which took place on september 24 25, saw speakers from across the globe. Figure 1. owasp top 10 web application security risks mapping from 2017 to 2021. here’s the recap of the changes from owasp site: a01:2021 broken access control moves up from the fifth position; 94% of applications were tested for some form of broken access control. the 34 common weakness enumerations (cwes) mapped to broken access control.

Owasp Top 10 Security Vulnerabilities 2021 Evalian Non profit confirms latest iteration of web attack hit list during 24 hour live event. owasp celebrated its 20th anniversary last week with a 24 hour webinar that saw the organization officially launch the top 10 web security vulnerabilities for 2021. the online conference, which took place on september 24 25, saw speakers from across the globe. Figure 1. owasp top 10 web application security risks mapping from 2017 to 2021. here’s the recap of the changes from owasp site: a01:2021 broken access control moves up from the fifth position; 94% of applications were tested for some form of broken access control. the 34 common weakness enumerations (cwes) mapped to broken access control.

Owasp Top 10 Vulnerabilities 2021 Revealed Infosectrain

Comments are closed.