Performing A Security Assessment Of The Cloud Using The Risk Management Framework A Case Study

Performing A Security Assessment Of The Cloud Using The Risk Management Risk assessment (h2): the unique element of risk assessment in cloud computing relates to the operational security and monitoring of cloud services. security assessments are important mechanisms for risk mitigation from cloud security breaches, which can be undertaken using an information risk management framework (zhang et al., 2010). Through a meticulous analysis of 21 scholarly papers, we explore various aspects of security risk assessment for the cloud. the results provide valuable insights into delivery models, standards, and validation practices, contributing to a comprehensive understanding of cloud risk assessment.

Cloud Security Assessment 8 Step Process And Checklist Performing a security assessment of the cloud using the risk management framework a case study awspssummit singapore download as a pdf or view online for free submit search performing a security assessment of the cloud using the risk management framework a case study awspssummit singapore. This case study emphasized the importance of effectively addressing security challenges in the field of cloud computing., stimulating further research in cloud security. additionally, another study by alrasheed et al. citation 23 have performed an analysis study concentrating on different deployment methods for intelligent devices in cloud. About press copyright contact us creators advertise developers terms privacy policy & safety how works test new features nfl sunday ticket press copyright. The first step in the framework is to formulate and communicate a vision for the cloud at an enterprise and business unit level. the first two principles relate to this vision: 1. executives must have oversight over the cloud —the business as a whole needs to recognise the value of the cloud based technology and data.
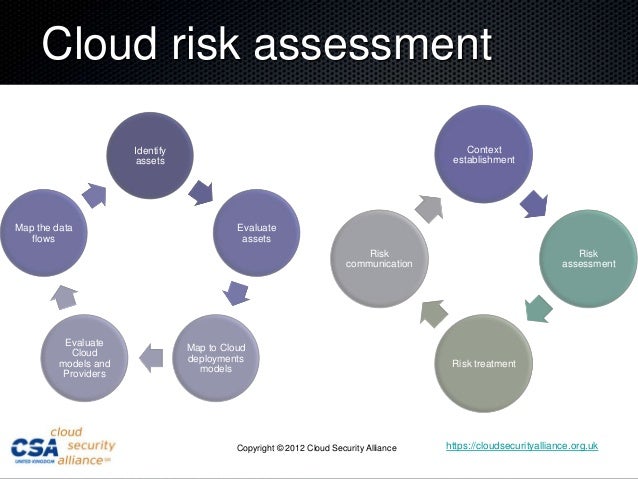
Cloud Risk Assessment Identify Context About press copyright contact us creators advertise developers terms privacy policy & safety how works test new features nfl sunday ticket press copyright. The first step in the framework is to formulate and communicate a vision for the cloud at an enterprise and business unit level. the first two principles relate to this vision: 1. executives must have oversight over the cloud —the business as a whole needs to recognise the value of the cloud based technology and data. Case study analysis of the use of cloud computing for assessing big data risks a quantitative risk and impact assessment framework (quirc) is presented, to assess the security risks associated. Conclusion. businesses are realizing the power of cloud computing, and its use is increasing. this case study represents a one time attempt at risk assessment of the cloud computing arrangement. the risk assessment helped uncover some of the key risks, prioritize those risks and formulate a plan of action. given the evolving nature of risks in.
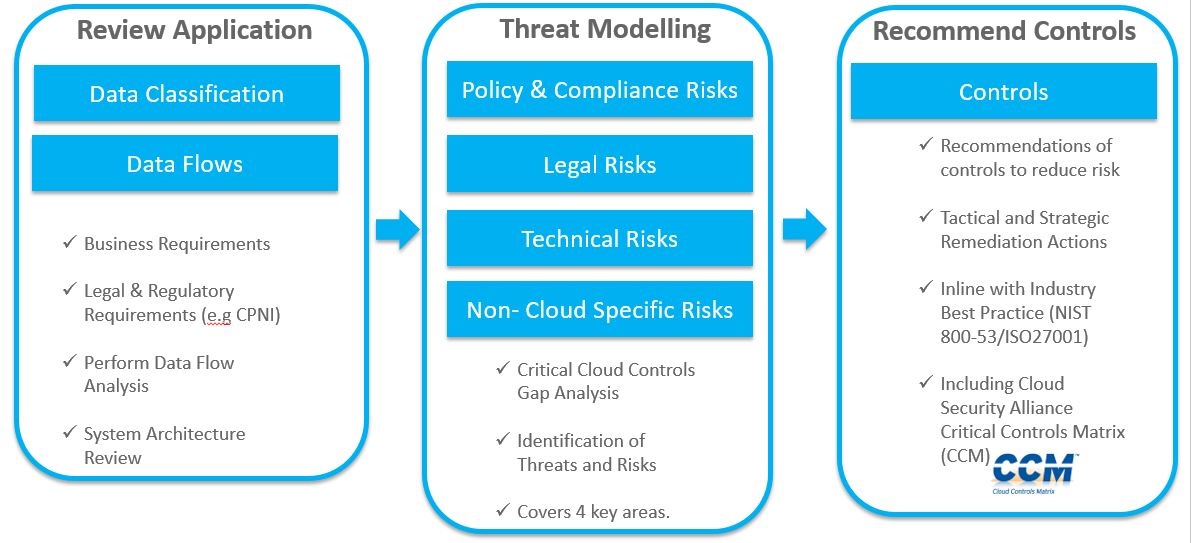
Cloud Security Risk Assessment Jaw Consulting Uk Case study analysis of the use of cloud computing for assessing big data risks a quantitative risk and impact assessment framework (quirc) is presented, to assess the security risks associated. Conclusion. businesses are realizing the power of cloud computing, and its use is increasing. this case study represents a one time attempt at risk assessment of the cloud computing arrangement. the risk assessment helped uncover some of the key risks, prioritize those risks and formulate a plan of action. given the evolving nature of risks in.

Comments are closed.