Stay Vigilant Be Diligent How To Protect Yourself From Phishing
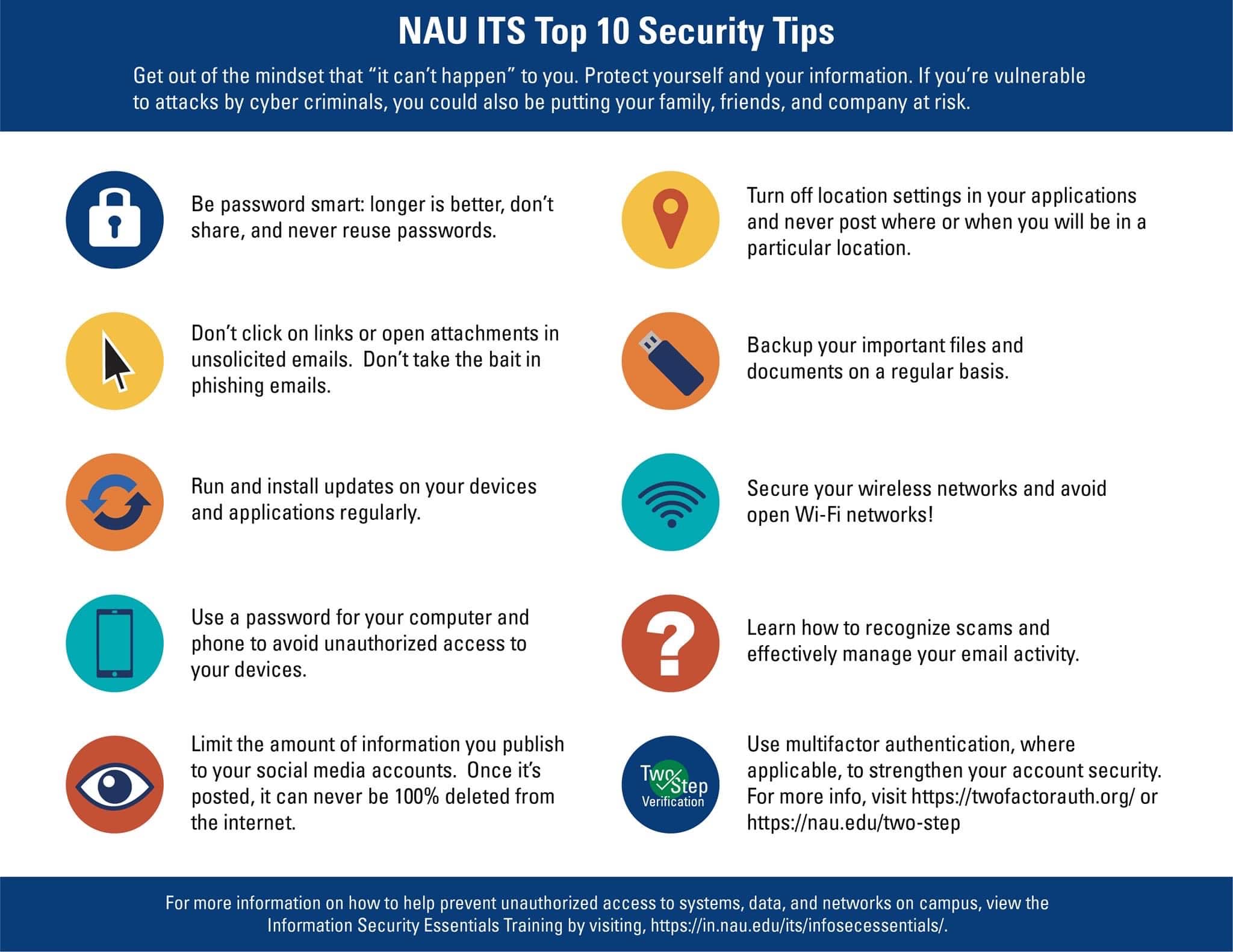
Stay Vigilant Be Diligent How To Protect Yourself From Phishing 14. regularly back up your data. routinely backing up your data is a good way to increase your peace of mind and help protect against the damage of phishing attacks. that way, if something goes wrong with your device, you’ll know that you’ll still have access to all your important files and data. 15. One of the best ways to protect your online accounts is by practicing good password hygiene. here’s how: set strong passwords: they should be at least 14 characters long and contain a mix of letters, numbers, and special characters. change your passwords often. use a unique password for every site, and never share your passwords with anyone else.

Stay Vigilant Be Diligent How To Protect Yourself From Phishing Do not fall for scams that may include purchasing gift cards for others. remember nau will not ask for your credentials over email or over the phone. report any suspicious emails. view security tips below for added protection. report potential phishing emails to the nau phish report application or call the solution center at (928) 523 1511 with. Make money from the small percentage of recipients that respond to the message. run phishing scams – in order to obtain passwords, credit card numbers, bank account details and more. spread malicious code onto recipients’ computers. spam phishing is one of the more popular means that scammers get your info. Educate yourself: stay informed about the latest phishing tactics. the more you know, the harder it is for scammers to trick you. stay alert to evolving techniques: with the rise of ai, phishing attacks are becoming more sophisticated. scammers can craft more convincing messages that are harder to detect, so always remain vigilant and trust. Alternatively, a phishing attack may claim someone has a tax refund waiting, requiring them to click on a link — which then might release a virus or malware that can infect the person’s computer. with so many variations of phishing attacks, it's important to stay vigilant online and when dealing with digital communications.

How To Protect Yourself From Phishing Educate yourself: stay informed about the latest phishing tactics. the more you know, the harder it is for scammers to trick you. stay alert to evolving techniques: with the rise of ai, phishing attacks are becoming more sophisticated. scammers can craft more convincing messages that are harder to detect, so always remain vigilant and trust. Alternatively, a phishing attack may claim someone has a tax refund waiting, requiring them to click on a link — which then might release a virus or malware that can infect the person’s computer. with so many variations of phishing attacks, it's important to stay vigilant online and when dealing with digital communications. 5. hover over links to verify the url. on computers and laptops, you can hover your cursor over links without clicking on them to see the web address. take a close look at the addresses the message is using. if it’s an email, look at the email address. maybe the address doesn’t match the company or organization at all. Whale phishing is similar to spear phishing, with a few notable differences. while spear phishing is generally aimed at members of a group, whale phishing is focused on a specific individual—usually the “biggest phish” at the target organization or an individual with significant wealth or power that the attackers wish to leverage.

Phishing Protection Checklist How To Protect Yourself From Phishing 5. hover over links to verify the url. on computers and laptops, you can hover your cursor over links without clicking on them to see the web address. take a close look at the addresses the message is using. if it’s an email, look at the email address. maybe the address doesn’t match the company or organization at all. Whale phishing is similar to spear phishing, with a few notable differences. while spear phishing is generally aimed at members of a group, whale phishing is focused on a specific individual—usually the “biggest phish” at the target organization or an individual with significant wealth or power that the attackers wish to leverage.

Comments are closed.