Tips For Developing And Reviewing Security Assessment Plan Sap

Tips For Developing And Reviewing Security Assessment Plan Sap Youtube In this video we went over some basic tips for developing and reviewing security assessment plan (sap). the sap is developed and approved prior to the securi. In the fedramp process, the 3pao creates a testing plan using the fedramp security assessment plan (sap) template. the sap template assists with providing the right level of detail to properly prepare for testing and documents: • activities planned for an assessment and the rules and boundaries for assessors.
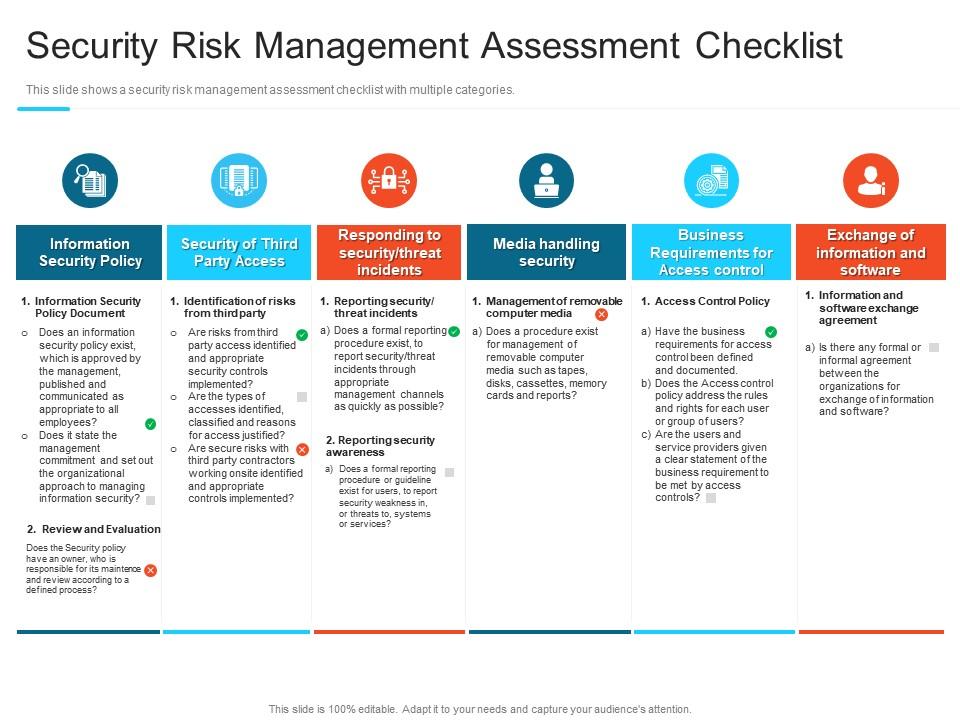
Security Risk Management Assessment Checklist Steps Set Up Advanced 4. security assessment plan (sap) overview – 200b 5. security assessment report (sar) overview – 200c 6. how to write to a control 7. continuous monitoring overview • the goal of the fedramp training series is to provide a deeper understanding of the fedramp program and how to successfully complete a fedramp authorization package assessment. 200 b: security assessment plan (sap) this course is designed to help fedramp recognized 3pao assessors understand how to write specific sections of a security assessment plan (sap) document, which contains the test plan to assess the security controls of a system. in addition, this course will cover the program’s reporting requirements for a. The csp will then develop a poa&m based on the sar findings. the poa&m documents the csp’s plan and timeline for remediating residual risk that remained at the conclusion of the security assessment. 12.0 agency authorization process 12.1 agency review of security authorization package. Use the description tab on the left side of the screen to read a detailed description of the screen elements including the image descriptions, screen text, and audio script. you may also access the resources button at the top right corner of the screen to open additional course resources. when you are finished, click the next arrow to continue.
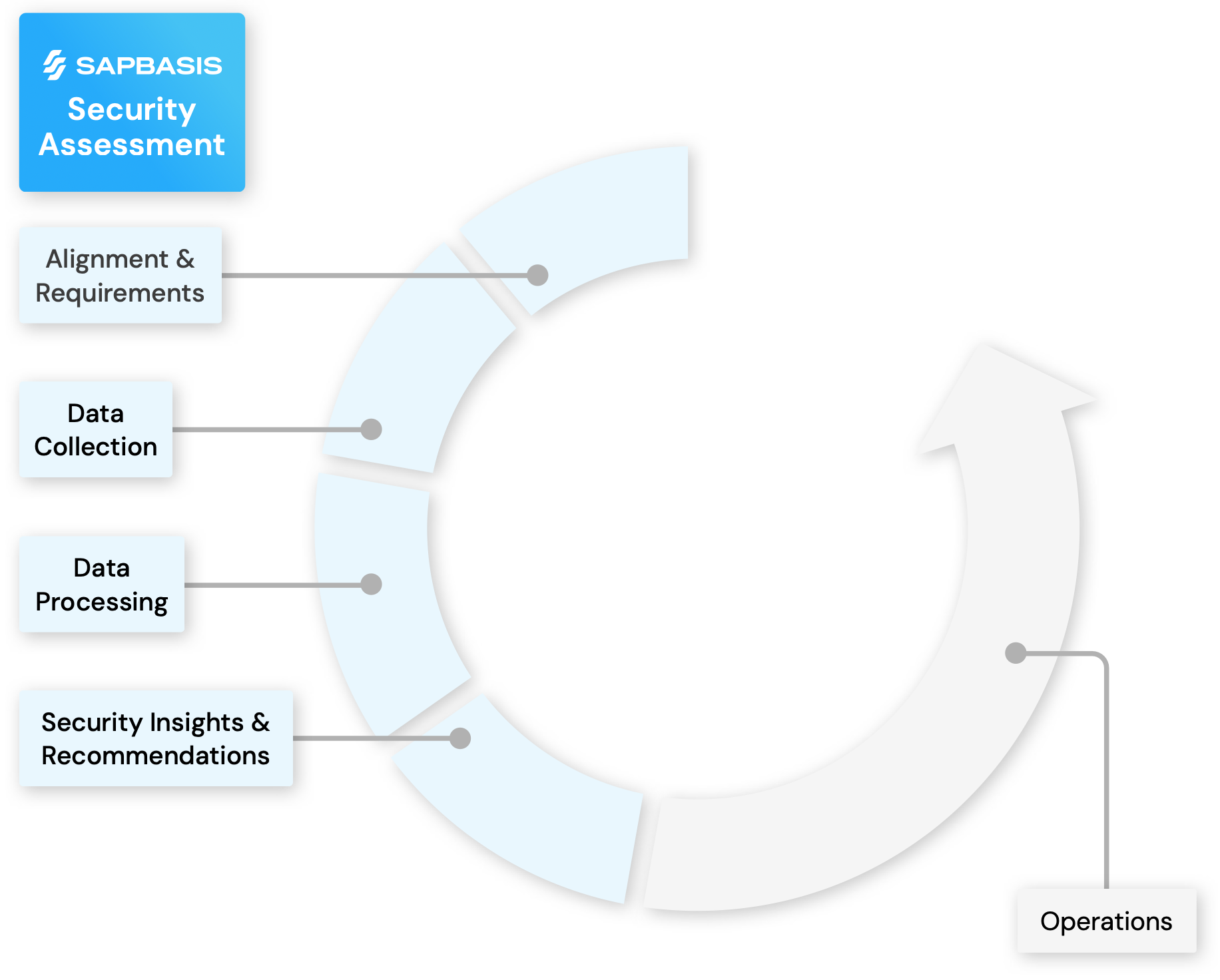
Sap Security Assessment Sap Basis The csp will then develop a poa&m based on the sar findings. the poa&m documents the csp’s plan and timeline for remediating residual risk that remained at the conclusion of the security assessment. 12.0 agency authorization process 12.1 agency review of security authorization package. Use the description tab on the left side of the screen to read a detailed description of the screen elements including the image descriptions, screen text, and audio script. you may also access the resources button at the top right corner of the screen to open additional course resources. when you are finished, click the next arrow to continue. Federal risk and authorization management program (fedramp) compliance is a complex journey that requires several key documents and deliverables. two of the most important are the security assessment plan (sap) and the security assessment report (sar). the sap and the sar play pivotal roles in ensuring cloud offerings undergo a thorough. As mentioned previously, the ssp is the foundational document that supports a fedramp assessment. the ssp is used by a 3pao to develop a security assessment plan (sap). therefore the ssp must provide sufficient detail on how each control is implemented in order for the 3pao to develop a test approach for the control.
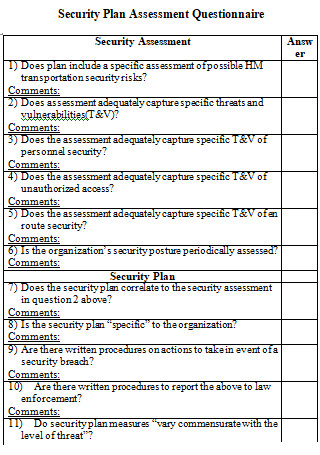
23 Sample Security Assessment Plan In Pdf Ms Word Federal risk and authorization management program (fedramp) compliance is a complex journey that requires several key documents and deliverables. two of the most important are the security assessment plan (sap) and the security assessment report (sar). the sap and the sar play pivotal roles in ensuring cloud offerings undergo a thorough. As mentioned previously, the ssp is the foundational document that supports a fedramp assessment. the ssp is used by a 3pao to develop a security assessment plan (sap). therefore the ssp must provide sufficient detail on how each control is implemented in order for the 3pao to develop a test approach for the control.
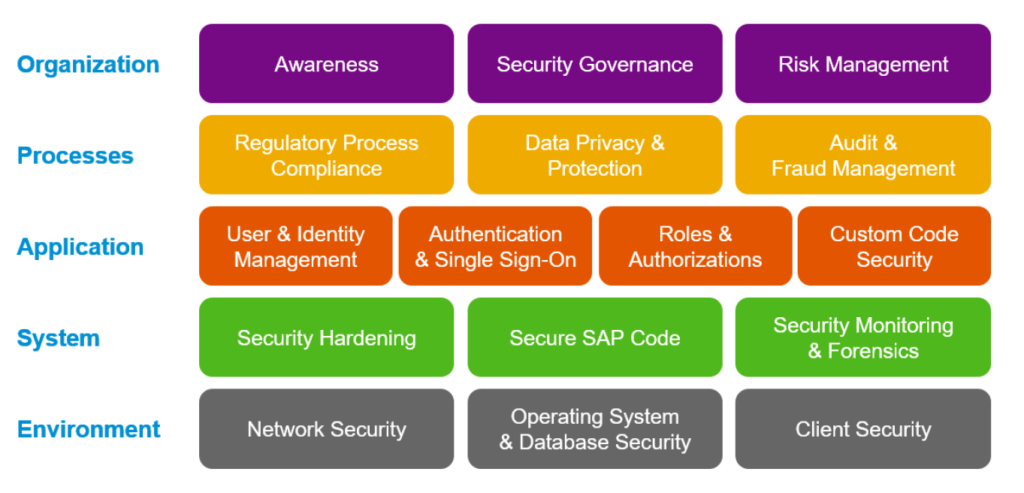
Sap Security Baseline Template Saptechnicalguru

Comments are closed.