What Is Pretexting How To Protect Yourself From Pretexting

What Is Pretexting How To Protect Yourself From Pretexting Youtube Pretexting, as a powerful form of social engineering, preys on trust and human psychology to extract sensitive information. by understanding what pretexting is and how it works—beyond its definition, you can take steps to protect yourself and your organization from falling victim to these attacks. Pretextingis form of social engineering in which an attacker fabricates a story to convince a victim to give up valuable information or access to a service or system. the distinguishing feature of.
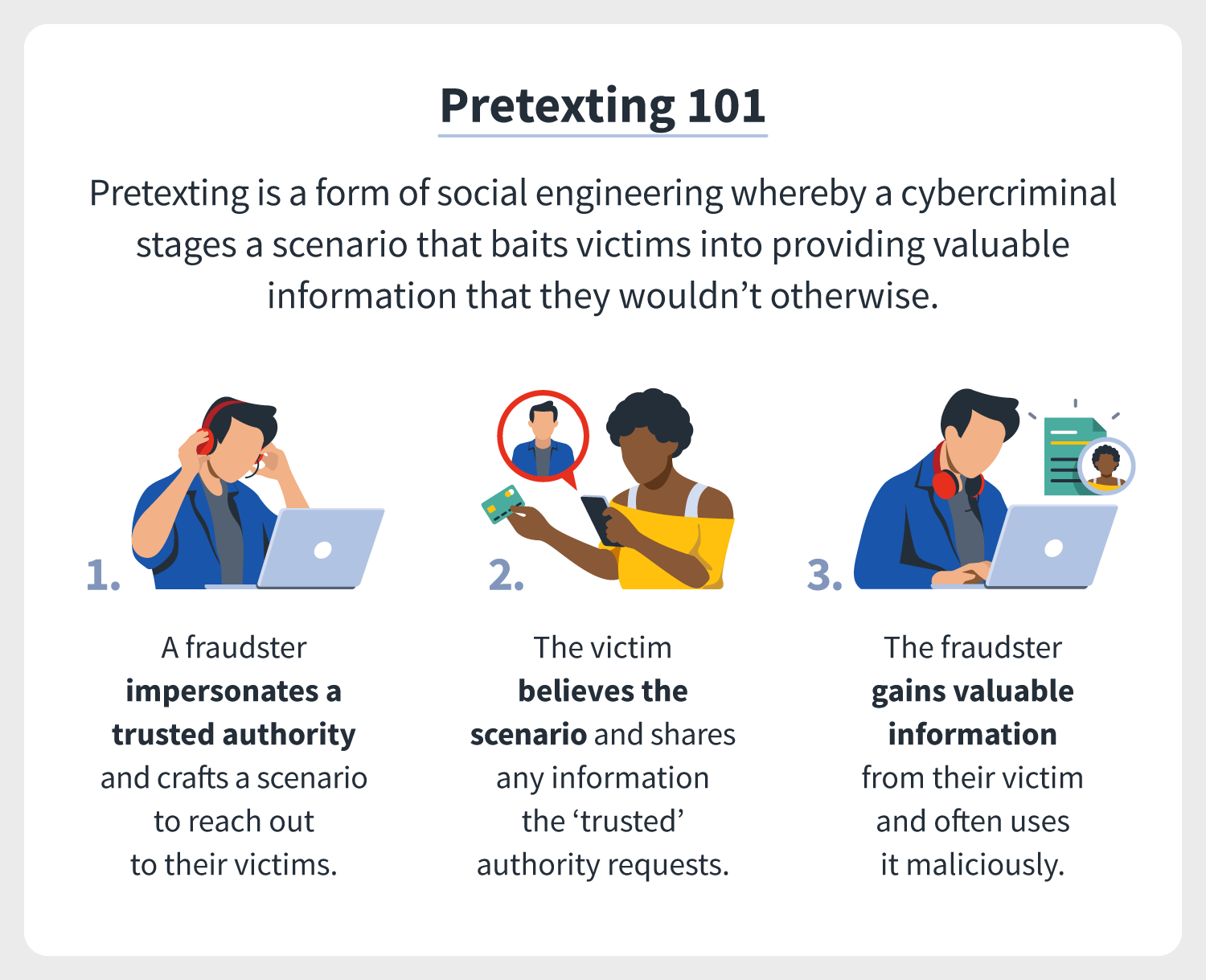
What Is Pretexting Definition Examples Prevention Tips Norton Pretexting is a type of social engineering attack that involves a criminal creating a story, or pretext, that manipulates their target into sharing personal data like passwords, credit cards, and logins. the attacker will come up with a scenario beforehand that seems believable and can exploit your trust in a person, company, or service. There are various pretexting techniques scammers and hackers use to gain access to sensitive information. 1. vishing and smishing. these techniques are very similar. vishing attacks involve using voice calls to persuade a victim to give up the information needed by the scammer. Pretexting is a social engineering attack where a cybercriminal creates a fabricated story to bait their target into revealing sensitive personal or proprietary information, sending money, or downloading malware. this puts the target at risk for identity theft, financial fraud, and future attacks. follow this guide to learn more about. Below are a few specific examples of steps you can take to prevent an attack causing damage to you or your business. here’s how to avoid a pretexting attack: establish security protocols, policies, and procedures for handling sensitive information. do not divulge sensitive information to unverified entities via email, phone, or text messages.

What Is Pretexting In Cyber Security Definition Attack Types Pretexting is a social engineering attack where a cybercriminal creates a fabricated story to bait their target into revealing sensitive personal or proprietary information, sending money, or downloading malware. this puts the target at risk for identity theft, financial fraud, and future attacks. follow this guide to learn more about. Below are a few specific examples of steps you can take to prevent an attack causing damage to you or your business. here’s how to avoid a pretexting attack: establish security protocols, policies, and procedures for handling sensitive information. do not divulge sensitive information to unverified entities via email, phone, or text messages. Avoiding pretexting altogether ensures your utmost cybersafety. here’s how to prevent pretexting: awareness and training: invest time for yourself and your employees to learn what cyber security is and why it is important. this essential knowledge can help you and others to recognize the signs of pretexting and to be cautious when revealing. Specifically, pretexting involves creating a credible false scenario to build the victim’s trust, often enhancing the effectiveness of phishing attacks by making them seem more legitimate. in essence, phishing represents the act of launching the attack, while pretexting is one of the social engineering methods that can be used in phishing.

What Is Pretexting In Social Engineering Glossary Avoiding pretexting altogether ensures your utmost cybersafety. here’s how to prevent pretexting: awareness and training: invest time for yourself and your employees to learn what cyber security is and why it is important. this essential knowledge can help you and others to recognize the signs of pretexting and to be cautious when revealing. Specifically, pretexting involves creating a credible false scenario to build the victim’s trust, often enhancing the effectiveness of phishing attacks by making them seem more legitimate. in essence, phishing represents the act of launching the attack, while pretexting is one of the social engineering methods that can be used in phishing.

What Is Pretexting How Does It Work By Craw Security Medium

Comments are closed.